You may have heard of a social engineering technique called “phishing” in which hackers attempt to trick you into revealing personal login information, which they then use to defraud you in some way. These phishing attacks usually take the form of an email which purports to be from a known and trusted organisation such as your bank or an online retailer.
I received one such email this morning and I wanted to share it with you to demonstrate just how realistic they can seem:
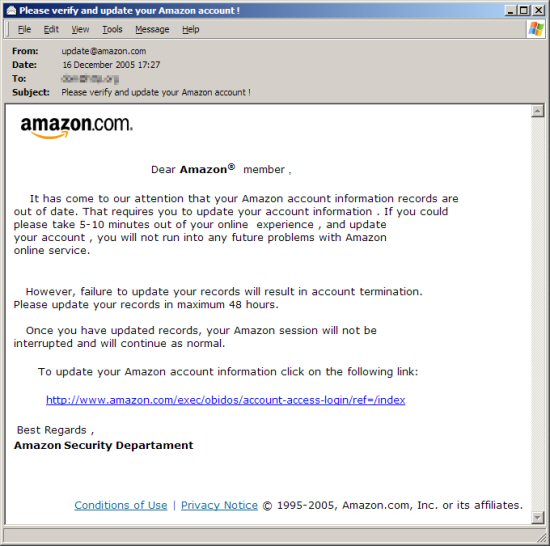
This email may look legitimate enough, but the embedded link actually takes you to a fake site which is intended to steal your login information and credit card details. In this case the rogue server is hosted at the NongMin Daily Newspaper Office in China, which presumably has been compromised.
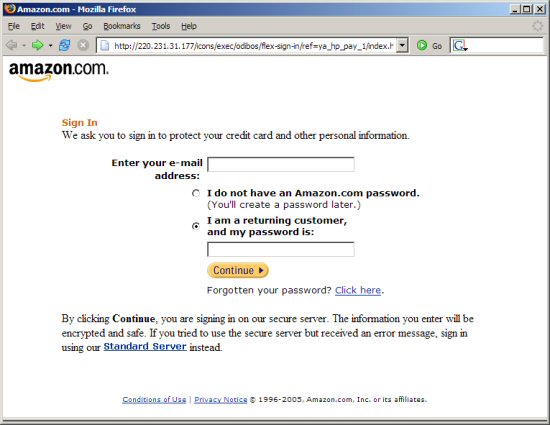
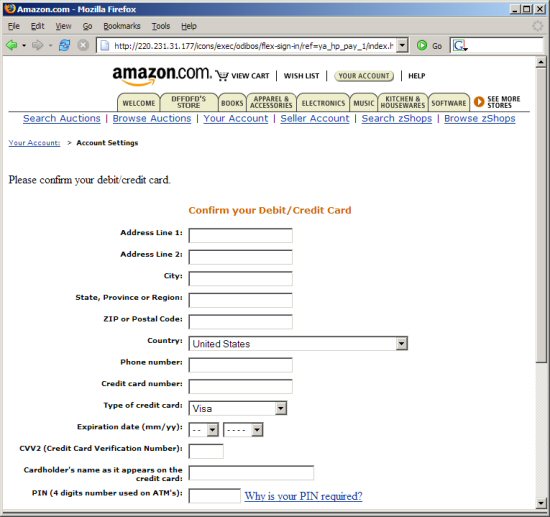
Please follow this advise to stay safe:
- Do not trust “From” addresses as these can easily be faked.
- Never divulge personal or banking details in response to an email.
- Do not click on links or attachments that you receive in unsolicited emails.